Why 95% of Domains Never Reach DMARC Enforcement
Why domains get stuck at p=none and how to reach enforcement.
Here’s a number that should bother you: according to recent research from EasyDMARC, over 80% of domains either have no DMARC record at all or are stuck at p=none. Among the top 1.8 million domains globally, 508,000 are in monitoring mode while only 350,000 have moved to actual enforcement.
That’s a lot of companies who started something and never finished it.
DMARC adoption has been growing fast. Google and Yahoo’s bulk sender requirements doubled adoption rates in early 2024. But adoption isn’t the same as protection. A DMARC record set to p=none does exactly one thing: it tells you that you have a problem. It doesn’t actually stop anything.
So why do so many domains get stuck?
The monitoring trap
When you first set up DMARC, the standard advice is to start with p=none. Makes sense. You want to see what’s happening before you start blocking things. The reports flow in. You see who’s sending email as your domain. You might even feel productive for a week or two.
Then reality sets in.
The reports are XML files that look like they were designed to be read by machines, not humans. Your marketing team added a new ESP last month and forgot to tell IT. Your CRM is sending email through some third-party service you’ve never heard of. And somewhere in the data, there’s an IP address in Eastern Europe sending 500 emails a day as your CEO.
Most teams look at this mess and decide they’ll deal with it later. Later never comes.
The vendor coordination problem
Here’s what nobody tells you when you start DMARC: reaching enforcement isn’t really a technical problem. It’s a coordination problem.
Your domain doesn’t just send email from one place. It sends email from your email provider, your marketing automation platform, your CRM, your support desk, your transactional email service, and probably three other tools someone signed up for years ago. Each of those services needs to authenticate correctly for DMARC to pass.
Getting them all aligned means talking to vendors. And vendors don’t always make this easy.
You open a support ticket explaining that DKIM isn’t aligned. The support rep asks you to “check your DNS settings.” You explain that you’ve checked your DNS settings and the problem is on their end. They escalate. You wait. A week later, someone asks you to check your DNS settings again.
This is where most DMARC projects die. Not because the technology is hard, but because coordinating with external vendors who don’t prioritize your authentication problems is exhausting.
The fix here isn’t more technical knowledge. It’s better communication tools. When you can hand a vendor a shareable dashboard showing exactly what’s failing and why, in language their support team understands, things move faster.
Fear of breaking legitimate email
The other killer is fear. Specifically, the fear that moving to p=quarantine or p=reject will break something important.
This fear isn’t irrational. If you flip to p=reject before all your legitimate senders are properly authenticated, you will block real email. The CEO’s newsletter doesn’t go out. Customer invoices bounce. Someone gets fired.
So teams stay at p=none indefinitely, telling themselves they’ll move to enforcement “once we’re sure everything is configured correctly.” But they’re never sure, because they’re never really looking at the data, because the data is hard to interpret, because they’re busy with other things.
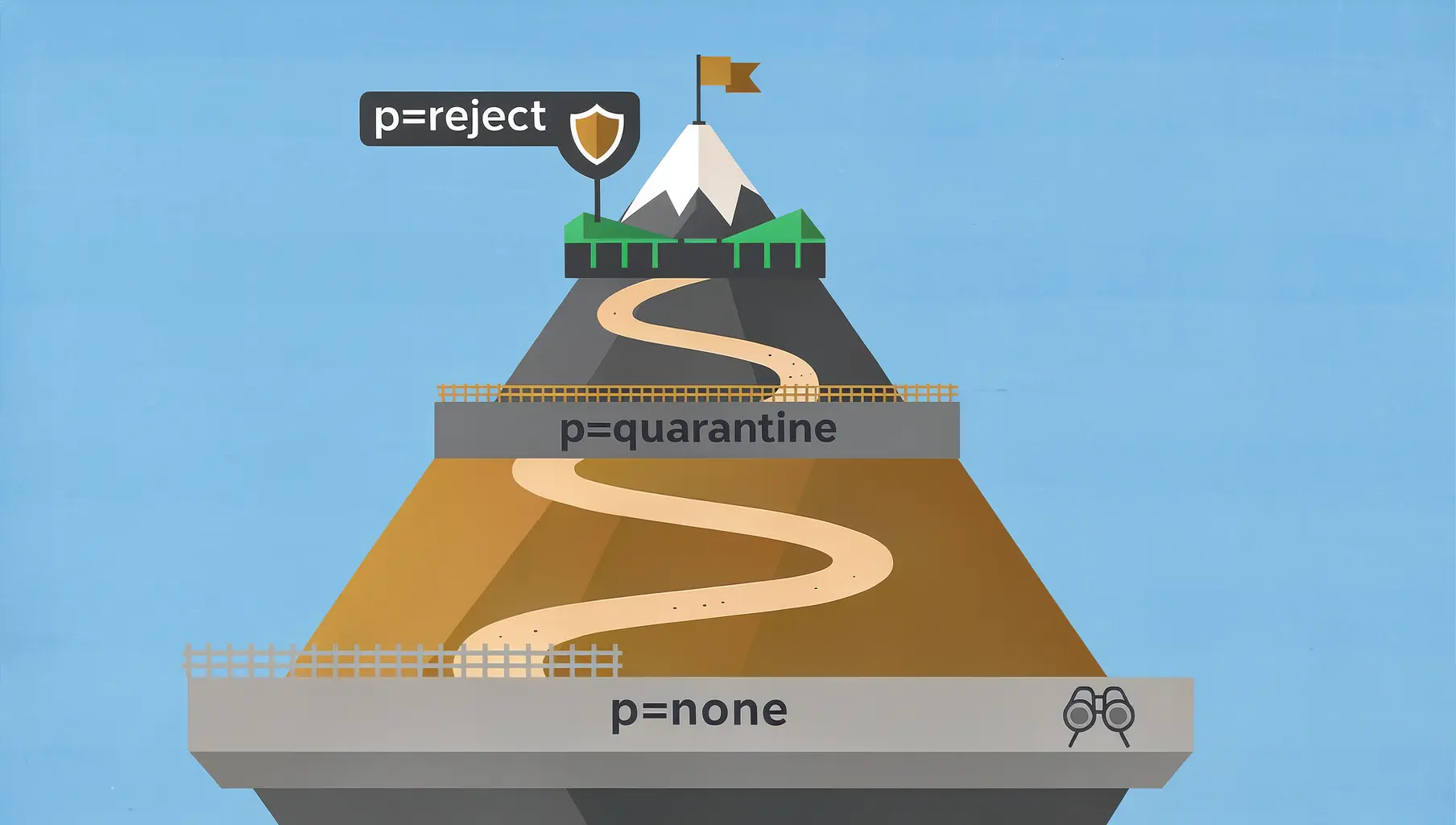
The way out is incremental. You don’t jump from p=none to p=reject. You move to p=quarantine first, maybe with pct=10 so only 10% of failing messages get quarantined. You watch for problems. You fix what breaks. You increase the percentage. Eventually, you get to p=reject.
This takes time. Valimail’s research suggests 75-80% of domains that publish DMARC records never make it through this process. They start monitoring and simply never finish.
The “good enough” fallacy
Some teams convince themselves that p=none is good enough. After all, they’re collecting reports. They can see what’s happening. That’s visibility, right?
Sort of. But visibility without action is just watching your house burn down through a window.
Countries that have mandated DMARC enforcement saw phishing success rates drop from 69% to 14%. That’s the difference between monitoring and enforcement. One shows you the problem. The other actually stops it.
And here’s the business case: organizations with DMARC at enforcement often see deliverability improve by 5-10%. Email providers trust authenticated senders more. Your marketing emails land in inboxes instead of spam folders. The upside isn’t just security. It’s revenue.
What actually works
The domains that reach enforcement share a few characteristics.
First, they treat DMARC as a project with a deadline, not an ongoing initiative. “We will be at p=reject by Q3” is a different energy than “we’re working on email authentication.” Projects end. Initiatives drift.
Second, they identify all their sending sources upfront. This means actually looking at the DMARC reports and building a list of every service that sends email as their domain. Most companies are surprised by what they find. That survey tool from 2019? Still sending email. The old marketing platform you migrated away from? Still in your SPF record.
Third, they have a system for vendor coordination. This might be a spreadsheet tracking which vendors have been contacted and what their status is. It might be vendor reports you can forward to support teams. The point is that getting vendors to fix their authentication becomes someone’s job, not something that happens when people remember.
Fourth, they move incrementally. Start at p=none. Move to p=quarantine at pct=10. Increase to pct=25, then 50, then 100. Watch for problems at each step. Fix what breaks. Then move to p=reject with the same gradual approach.
This isn’t complicated. It just requires someone to actually do it.
The enforcement gap is a competitive advantage
Here’s the thing about that 80% number: it means most of your competitors aren’t protected either.
Business email compromise cost organizations $2.77 billion in reported losses in 2024 alone. Phishing remains the entry point for most ransomware attacks. When attackers want to impersonate your company, they check if you have DMARC at enforcement. If you don’t, you’re an easy target.
Being in the 20% that actually finishes the job isn’t just about security. It’s about being the kind of organization that follows through on things. The kind that doesn’t leave half-finished projects lying around. The kind that vendors and customers can trust.
The destination is enforcement. The question is whether you’re going to get there.
Stop monitoring. Start enforcing.
Verkh helps you move from p=none to p=reject without the coordination headaches. Identify every sending source, generate vendor reports that actually get results, and track your progress toward full enforcement.
Related Articles
December 2025
p=none vs p=quarantine vs p=reject: Which DMARC Policy to Use
The three DMARC policies control what happens to failing email. Learn when to use each and how to safely progress to enforcement.
February 2026
DMARC for Healthcare: HIPAA Compliance and Email Security
How healthcare organizations can implement DMARC while meeting HIPAA requirements. Covers the Security Rule, vendor coordination, and the path to enforcement.
January 2026
Why You Need DMARC Enforcement Before BIMI Will Work
BIMI requires DMARC at p=quarantine or p=reject. Learn why and how to reach enforcement to display your logo in email.
Ready to implement this?
Verkh helps you monitor DMARC, identify issues, and reach enforcement. Start free.
Start Free