5 Key Benefits of Adopting an Email Authentication Platform Today
Why SPF, DKIM, and DMARC matter for security, deliverability, and brand protection. A practical guide for businesses of all sizes.

Email powers business communication. It also happens to be one of the easiest attack vectors for criminals to exploit. Phishing, domain spoofing, brand impersonation: these schemes cost organizations billions annually while destroying customer trust one fraudulent message at a time.
The solution? Email authentication platforms that implement SPF, DKIM, and DMARC to verify sender identity and protect your domain from unauthorized use.
Email authentication is hard. Anyone who tells you otherwise is either lying or selling you something that won’t work. It requires understanding your email ecosystem, coordinating with vendors, and progressively tightening policies without breaking legitimate mail flows.
But hard doesn’t mean impossible. With the right platform guiding you from monitoring to enforcement, you can protect your domain, improve deliverability, and stop criminals from weaponizing your brand. Here are five reasons to start today.
Understanding Email Authentication
What is Email Authentication?
Email authentication verifies whether a message comes from the domain it claims to represent. Three protocols form the foundation:
SPF (Sender Policy Framework) works like an employee directory for your domain. It publishes a list of IP addresses authorized to send email on your behalf. When a receiving server gets a message claiming to be from your domain, it checks this list.
DKIM (DomainKeys Identified Mail) adds a cryptographic signature to outgoing emails. This signature gets validated using a public key in your DNS records, confirming the message hasn’t been tampered with during transit.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) ties SPF and DKIM together with policy enforcement. It tells receiving servers what to do when authentication fails: deliver, quarantine, or reject. See our DMARC policy guide for a detailed breakdown of each option.
Why This Matters Now
The email landscape shifted when Google, Yahoo, and Microsoft began enforcing stricter sender requirements. Bulk senders transmitting more than 5,000 messages daily now need SPF, DKIM, and DMARC to reach inboxes. Non-compliant messages get routed to spam or rejected outright.
Beyond compliance, authentication addresses a fundamental flaw in email infrastructure. SMTP was designed decades ago without sender verification built in. That gap allowed bad actors to forge sender addresses with ease, spawning the phishing epidemic we’re dealing with today.
Authentication closes this vulnerability by creating verifiable links between messages and their origins. Organizations that implement these standards protect themselves and their recipients while building the sender reputation necessary for reliable inbox placement.
Benefit 1: Enhanced Email Security
Cyber threats targeting email grow more sophisticated daily. Attackers use generative AI to craft convincing phishing messages, impersonate executives with alarming accuracy, and launch business email compromise schemes that slip past traditional spam filters.
An email authentication platform provides the technical foundation to counter these threats.
Getting Authentication Right
Implementing email security requires a layered approach and a clear path from monitoring to enforcement.
Start with SPF by identifying every service authorized to send mail from your domain. Your primary mail server, marketing automation tools, CRM systems, transactional email services. All of them. Missing a legitimate sender creates delivery problems. Leaving unauthorized senders unaddressed opens security gaps.
Deploy DKIM signing across all outbound mail streams. Each sending service needs its own selector and key pair, with public keys published in DNS. This is where many organizations get stuck. They end up coordinating with vendors who don’t understand DMARC and won’t prioritize authentication requests.
Progress your DMARC policy deliberately. Begin with p=none to collect reports without affecting delivery. Analyze those reports to identify legitimate senders failing authentication. Fix the issues. Then move to p=quarantine and eventually p=reject as confidence grows.
This is where platforms like Verkh prove their value. Rather than leaving you to interpret XML reports and guess at fixes, Verkh shows you which senders are failing and why. Then it generates the copy-paste DNS records to fix them. The destination is enforcement, and every feature moves you toward p=reject.
How Authentication Stops Attacks
When properly configured, email authentication creates multiple barriers against common attack techniques.
Domain spoofing becomes nearly impossible when receiving servers enforce DMARC policies. An attacker forging your domain fails SPF checks because their server isn’t authorized. They lack valid DKIM signatures because they don’t have your private keys. With a DMARC reject policy, these fraudulent messages never reach their targets.
Brand impersonation faces similar obstacles. While attackers might register lookalike domains, authentication platforms increasingly monitor for these threats. They scan for domains visually similar to yours and alert your team before damage occurs.
Business email compromise exploiting compromised vendor accounts gets flagged through behavioral analysis. Modern platforms track communication patterns and alert when messages deviate from established norms.
The protection extends beyond your organization. When you authenticate outbound mail and enforce strict policies, you prevent criminals from weaponizing your domain against your customers, partners, and the broader email ecosystem.
Benefit 2: Improved Email Deliverability
Email deliverability determines whether your messages reach inboxes or disappear into spam folders. Authentication serves as a trust signal that mailbox providers evaluate when making filtering decisions.
How SPF, DKIM, and DMARC Work Together
Each protocol contributes distinct value.
SPF establishes baseline authorization by confirming messages originate from permitted infrastructure. Without valid SPF, receiving servers immediately view your mail with suspicion. But SPF has limitations. It checks the envelope sender rather than the visible “From” address, and it breaks during forwarding.
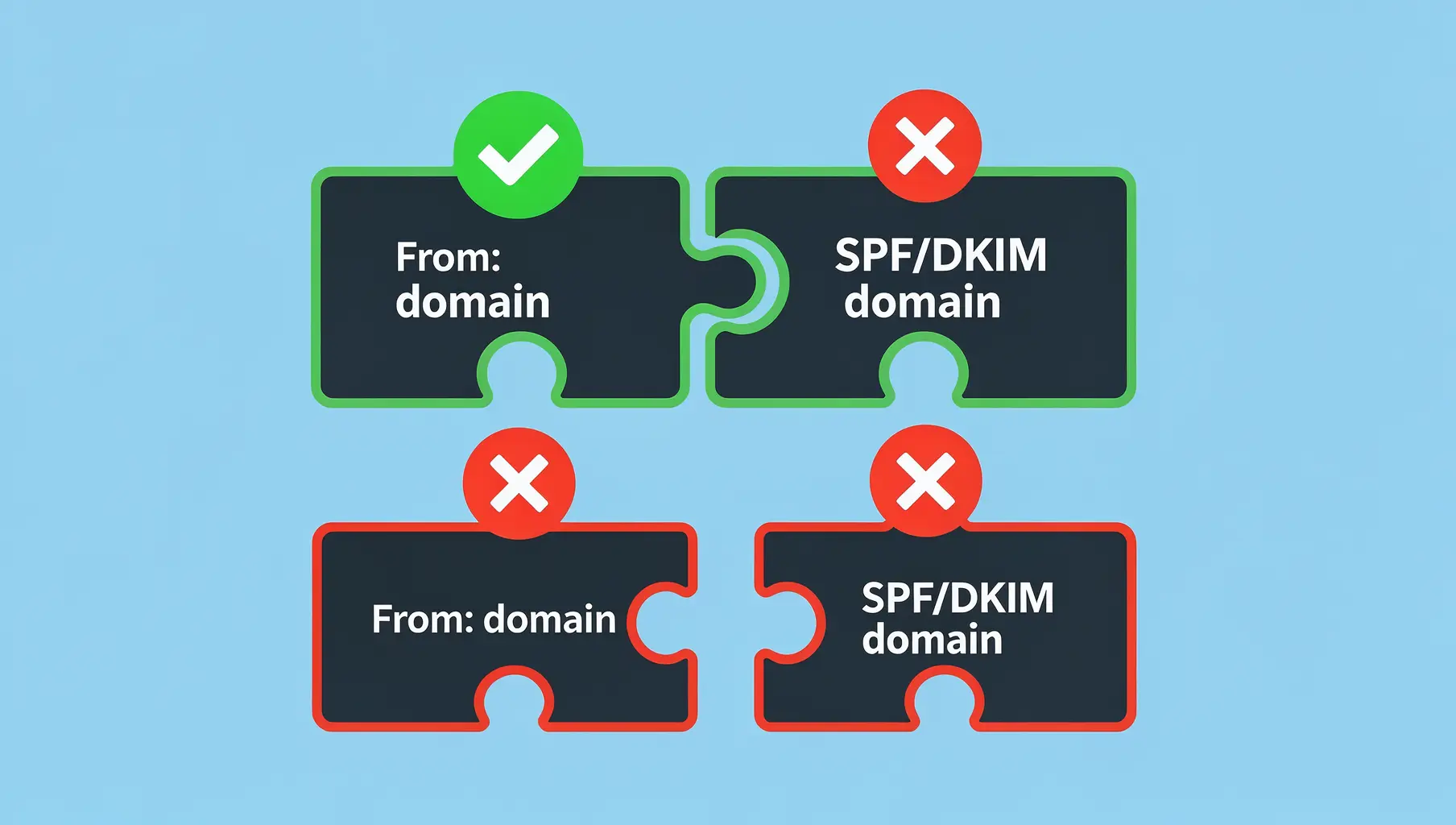
DKIM addresses these shortcomings by authenticating the message itself. The cryptographic signature survives forwarding, and DKIM alignment verifies the visible sender domain matches the signing domain.
DMARC unifies these checks and adds alignment requirements that prevent attackers from exploiting gaps between envelope and header addresses. It also generates aggregate reports showing authentication results across all mail claiming your domain.
Together, these protocols demonstrate to mailbox providers that you maintain proper technical hygiene. This reputation translates into better inbox placement.
The Vendor Coordination Problem
Most authentication platforms won’t tell you this: the hardest part isn’t configuring your own systems. It’s getting your vendors to authenticate correctly.
Your ESP says it’s your DNS. Your DNS provider says it’s your ESP. Your marketing platform’s support team doesn’t know DMARC from DNS. Meanwhile, you’re stuck at p=none with authentication failures you can’t explain to people who don’t understand the problem.
This is the gap Verkh addresses. Instead of generating cryptic reports you have to interpret yourself, Verkh creates vendor-ready remediation reports. These documents explain what’s broken in terms support reps understand. They include the specific evidence, the steps to fix the issue, and links to the vendor’s own setup documentation.
Even better, Verkh’s Apex shareable dashboards let you share a live link with vendors instead of emailing static PDFs that get lost in threads. Vendors see real-time authentication status, the data updates automatically as they make fixes, and you know the moment they view it. No competitor offers this.
Organizations moving to DMARC enforcement typically see delivery rate increases of 5-10% for marketing campaigns alone. The combination of proper authentication and effective vendor coordination accelerates this timeline.
Benefit 3: Protection Against Brand Impersonation
Your brand represents years of investment in customer relationships and trust. Cybercriminals recognize this value and increasingly target established brands for impersonation attacks.
How Impersonation Works
Brand impersonation occurs when attackers craft messages appearing to originate from legitimate organizations. These attacks exploit the trust customers place in familiar brands to extract sensitive information, credentials, or payments.
Common techniques include:
Sender name spoofing displays a recognized brand name while using an unrelated email address. Casual recipients see the familiar name and engage without checking the actual sender.
Domain spoofing forges the sending domain itself, making messages appear to come from the impersonated organization. Without authentication enforcement, receiving servers can’t detect this forgery.
Lookalike domains register addresses visually similar to legitimate brands by swapping letters, adding characters, or using different TLDs. These are harder to detect because the sending domain technically exists.
The consequences extend beyond immediate fraud losses. Customers receiving phishing emails that appear to come from your domain lose trust in legitimate communications. They may ignore authentic security alerts, miss important updates, or take their business elsewhere.
Authentication as Brand Defense
DMARC enforcement at p=reject provides the strongest protection against direct domain spoofing. When you publish a reject policy, receiving servers block messages that fail authentication. This prevents criminals from sending mail that appears to originate from your exact domain.
But enforcement alone isn’t enough. You need visibility into who’s attempting to use your domain and whether those attempts are legitimate senders with configuration problems or actual attacks.
Verkh provides this visibility through DMARC reporting that identifies senders by name rather than just IP address. You see “SendGrid” or “Mailchimp” instead of deciphering ASN numbers. Legitimate senders with fixable problems get remediation guidance. Suspicious activity gets flagged for investigation.
For organizations at Enterprise tiers, Verkh’s Apex dashboards add another layer of brand protection. When you need to coordinate authentication fixes with vendors, you share a live dashboard instead of static reports. View analytics show when vendors access the information, creating accountability that PDFs can’t provide.
The path from monitoring to enforcement protects your brand progressively. Each policy upgrade, from p=none to p=quarantine to p=reject, reduces the attack surface criminals can exploit while you verify legitimate mail flows remain intact.
Benefit 4: Simplified Email Validation and Management
Email authentication addresses sender verification, but organizations also need efficient tools to manage the authentication process itself. The complexity of coordinating multiple sending services, maintaining DNS records, and interpreting DMARC reports creates operational burden that the right platform can eliminate.
The Management Challenge
Most organizations underestimate the ongoing work authentication requires. Adding new marketing tools, switching ESP providers, acquiring companies: each change demands authentication updates. DNS records drift. Vendors change their infrastructure. New services get deployed without proper DKIM configuration.
Without centralized management, these issues compound until authentication breaks in ways that aren’t immediately obvious. Marketing campaigns start landing in spam. Transactional emails go missing. By the time someone notices, sender reputation has already suffered.
Platform-Based Solutions
Modern authentication platforms address this complexity through automation and clear reporting.
Sender discovery identifies services sending mail as your domain, eliminating the guesswork of tracking down every system that might be using your address.
DNS management generates correct records and validates existing configuration, catching errors before they affect delivery.
Continuous monitoring alerts you when authentication starts failing, when new unauthorized senders appear, or when DNS records change unexpectedly.
Progress tracking shows your path from monitoring through enforcement, celebrating milestones at 90%, 95%, and 99% pass rates.
Verkh builds these capabilities on Cloudflare’s edge infrastructure, delivering sub-100ms response times globally with 99.99% uptime capability. The platform ingests DMARC reports, monitors DNS continuously, identifies sending sources, and tells you how to fix problems. Not just that problems exist.
Every tier from Free through Enterprise+ is self-service. No sales calls required. You sign up, add your domain, and start seeing your authentication status within minutes. Upgrade when you need more domains, more users, or advanced features like Apex dashboards. Downgrade or cancel anytime.
This accessibility matters because authentication shouldn’t be gatekept behind enterprise sales cycles and opaque pricing. Basic security should be available to organizations of all sizes.
Benefit 5: Future-Proofing Your Email Infrastructure
Email security requirements continue evolving as threats advance and regulatory frameworks expand. Organizations implementing authentication today position themselves ahead of tomorrow’s demands.
What’s Coming in 2025 and Beyond
Several developments will shape authentication requirements in the coming year.
Enforcement expansion continues as more mailbox providers follow Google, Yahoo, and Microsoft in requiring authentication. Regional providers and enterprise email systems are adopting similar policies, making authentication table stakes globally.
BIMI adoption grows as organizations seek competitive advantages in crowded inboxes. Brand Indicators for Message Identification displays verified logos alongside authenticated messages, increasing open rates. BIMI requires DMARC enforcement as a prerequisite, which is another reason to reach p=reject sooner rather than later.
AI-powered threats demand stronger authentication as attackers use generative AI for more convincing phishing. Authentication provides technical verification that compensates for increasingly sophisticated social engineering.
Regulatory requirements expand to mandate authentication in additional industries. Financial services, healthcare, and government sectors face growing compliance obligations that include email security controls. PCI DSS 4.0 already mandates DMARC for payment processors.
Building for Tomorrow
The organizations seeing the best results treat authentication as infrastructure rather than a one-time project. They choose platforms that grow with their needs, automate ongoing maintenance, and provide clear paths from current state to full enforcement.
Verkh is built for this trajectory. The Free tier lets you see your authentication status immediately: what’s passing, what’s failing, where the problems are. Starter adds guided remediation so you can fix issues yourself. Pro enables vendor reports and workspaces for managing multiple domains. Enterprise unlocks Apex shareable dashboards with view analytics, SSO, and API access.
Each tier builds on the previous one. You’re never locked into capabilities you don’t need, and you’re never blocked from features that would help. The pricing is transparent, the billing is self-service, and the focus stays on getting you to enforcement. Not keeping you dependent on the platform.
Conclusion
Email authentication delivers concrete benefits regardless of organization size. Enhanced security protects against phishing and spoofing. Improved deliverability ensures messages reach recipients. Brand protection prevents criminals from exploiting your reputation. Simplified management reduces operational burden. Future-proofing positions you ahead of evolving requirements.
The question isn’t whether to implement authentication. Major mailbox providers made that decision for you. The question is whether to struggle through implementation manually or use a platform that guides you from monitoring through enforcement.
Most DMARC tools stop at dashboards and visibility. They show you have a problem without showing you how to fix it. You’re left interpreting XML reports, guessing at DNS changes, and sending PDFs to vendors who ignore them.
Verkh takes a different approach. The destination is enforcement, p=reject, and every feature moves you toward it. Copy-paste DNS records instead of cryptic errors. Vendor remediation reports that support teams understand. Apex shareable dashboards that create accountability. Self-service pricing that doesn’t gatekeep security behind sales calls.
Email security is hard. We don’t pretend otherwise. But hard becomes manageable with the right guidance, the right tools, and a platform that walks with you until you reach the destination.
Start free at verkh.io: see your authentication status in 60 seconds, no credit card required.
Related Articles

January 2026
How to Ensure Your Emails Are Authenticated and Reach the Inbox
A practical guide to setting up SPF, DKIM, and DMARC so your emails actually get delivered. No fluff, just the steps that matter.
December 2025
DMARC Alignment Explained Simply
DMARC alignment determines whether SPF and DKIM results count. Learn relaxed vs strict alignment and when each matters.
December 2025
Third-Party Senders and DMARC: The Complete Guide
ESPs, CRMs, and marketing platforms send as your domain. Learn how to configure DMARC for third-party senders properly.
Ready to implement this?
Verkh helps you monitor DMARC, identify issues, and reach enforcement. Start free.
Start Free